Networking Guide
A practical, step-by-step walkthrough to create private networks, validate CIDR inputs, and understand how networking ties into your instances and security groups. This guide complements the overview at Networking.
1) Create a Private Network
Use a tenant-scoped private network to isolate your instances. You can let the platform auto-assign a CIDR, or request one explicitly in the 10.1.x.0/24 range.
- Open the dashboard and go to Menu → Network → Private Networks.
- Click "Create Network".
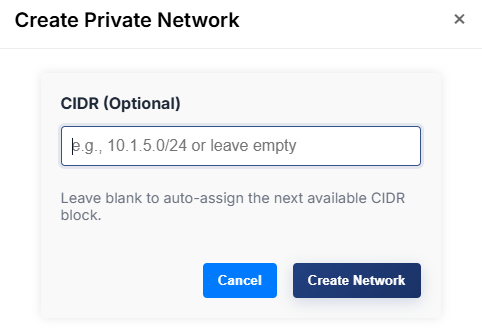
- (Optional) Enter a CIDR in the format
10.1.x.0/24(e.g.,10.1.5.0/24).- Allowed pattern:
^10\.1\.\d{1,3}\.0/24$ - If left blank, the next available block is auto-assigned.
- For most cases, just leave it blank
- Allowed pattern:
- Submit to create the network.
Tips:
- Keep a simple naming convention for networks to reflect environment (e.g.,
dev-net,prod-net).
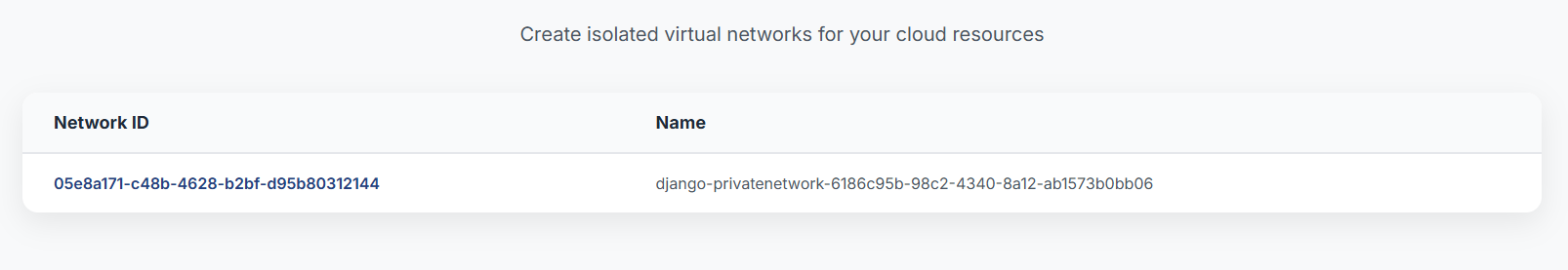
2) View Your Networks
After creation, your networks appear in the table/list with their IDs and names.
- Desktop: See Network ID and Name columns.
- Mobile: Tap a card to view details.
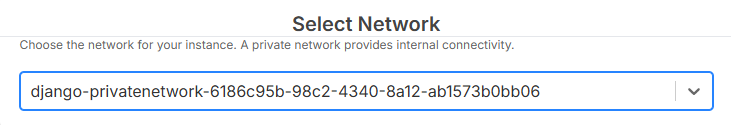
3) Launch Instances Into a Private Network
When creating an instance in Compute, select your private network to place the VM within that isolated environment. Combine with security groups to control access.
4) Security Groups (Firewall Rules)
- Create security groups and add inbound rules such as SSH (22) or HTTP (80).
- Attach security groups to instances to enforce least privilege.
- See Security Groups Guide.
5) Troubleshooting
- Invalid CIDR error when creating a network:
- Ensure it matches
10.1.x.0/24(e.g.,10.1.12.0/24). - Use only numbers for
x(0–255). The UI uses a regex similar to:^10\.1\.\d{1,3}\.0/24$.
- Ensure it matches
- Network creation fails intermittently:
- Try again after a short delay; check notifications for progress.
- Instance cannot reach another:
- Verify both are in the same private network or routing is set up.
- Confirm security group rules allow the traffic.
Related
- Networking Overview → About Networking
- Compute → Launch instances
- Security Groups → Firewall rules